DNS enumeration/DNS recon-reading
https://medium.com/p/55265457b29a/edit
DNS enumeration/DNS recon-reading
https://securitytrails.com/blog/dns-enumeration
1. Identify what kind of information we need to search through DNS tools, find out those definitions. 2. Find out all services that work behind the DNS 3. make an automation code for enumeration DNS
How DNS Works:
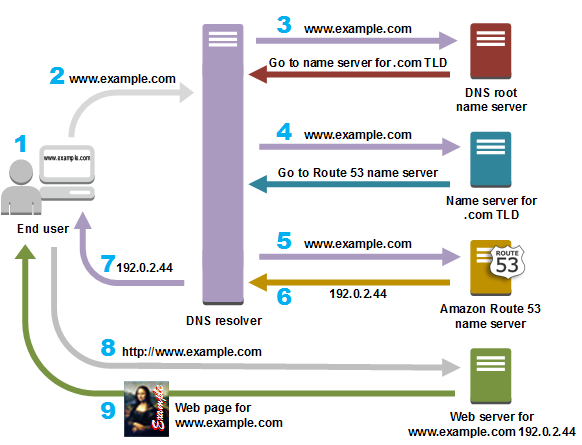
Authoritative Name server: DNS-records (aka zone files): DNS records (aka zone files) are instructions that live in authoritative DNS servers.
DNS Enumeration:
If the output of the command is greater than 1 it’s a good indicator that there might be a wildcard configuration. this means for the next step is that brute-forcing will return a lot of false positives. The reason for this is that the wildcard will match anything that is not a registered subdomain and point all of them to the same place.
If you look at this you can learn so much before even hitting the domain. Look at the A records and where DNS is hosted. These can contain hugely informative pointers such as:
Where is their mail hosted?
Where are they hosting DNS? Are they using a WAF or Proxy service like Cloudflare?
What platform are they hosting on? They might reuse this service for other things.
What countries/geo locations do they host in?
Is there any pattern to the type of subdomains? Can you try and enumerate more? For example (server1.mydomain.com), or (mustang.mydomain.com, charger.mydomain.com).
Where did they register the domain? Are there other domains registered from the same registrar?
Sublist3r,aiodnsbrute,subfinder,amass,full on DNS bruteforce using MassDNS or ZDNS.
Host
NsLookup
Dnsenum
Amass
https://www.dionach.com/blog/how-to-use-owasp-amass-an-extensive-tutorial/ https://hakluke.medium.com/haklukes-guide-to-amass-how-to-use-amass-more-effectively-for-bug-bounties-7c37570b83f7 https://www.hackingarticles.in/4-ways-dns-enumeration/ https://medium.com/@klockw3rk/back-to-basics-dns-enumeration-446017957aa3 https://delta.navisec.io/web-enumeration-reference/ https://0x00sec.org/t/what-is-your-go-to-dns-enumeration-methodology-discussion/20169/11
DNS vulnerabilities: AXFR (Asynchronous Transfer Full Range) Transfer Similar to zone transfer, there is a so-called NSEC walking attack, which enumerates DNSSEC-signed zones. DNS spoofing DNS hijacking and DNS server attacks such as domain fronting https://securitytrails.com/blog/most-popular-types-dns-attacks https://securitytrails.com/blog/risks-of-modern-free-ssl-certificates-and-stale-dns-records https://portswigger.net/daily-swig/dns https://securitytrails.com/blog/domain-tools
twits:
Here are the tools I am using and why! ShuffleDNS -> Active DNS Enumeration FFUF -> Content Discovery Gau -> Param & Endpoint Curl -> Check Mass Response Burp Suite -> Manual Lookup
2-Active Information Gathering: -Network tracing -DNS Enumeration -Reverse Lookup Brute Force -DNS Zone Transfers -Port Scanning -Network Sweeping -OS Fingerprinting -Service Enumeration -Banner grabbing ,etc

Google Search Strings: DNS attacks DNS vulnerabilities DNS Enumeration
TODO: https://www.youtube.com/watch?v=nlFAj2raoj4
Dictionary brute force:
In the dictionary brute force, we directly use the wordlist to a brute force domain name to find valid subdomains.
Tools:
Permutation brute force:
In permutation brute force, we create a new resolved subdomain list from already known subdomains/domains by using permutation, mutation, and alteration with a wordlist.
Tool:
Last updated